Two-thirds of customer-facing enterprise systems are bearing the majority of Distributed Denial-of-Service DDoS attacks of which 84 million were recorded in 2019 alone. An attack that targets multiple layers of the protocol stack at the same time such as a DNS amplification targeting layers 34 coupled with an HTTP flood targeting layer 7 is an example of multi-vector DDoS.
 T Mobile S Us Network Goes Down Impacting Verizon At T And Other Carriers Dcd
T Mobile S Us Network Goes Down Impacting Verizon At T And Other Carriers Dcd
A Distributed Denial-of-Service DDoS attack is one of the challenges you may encounter when using online services.
Ddos attacks today. The hacker behind the DDoS attack sends malware to numerous systems and if successfully installed can use that malware to remotely take over some or all of the compromised systems processes to carry out the attack. And confidently moved from last to second place 36 against 16 in the previous reporting period. Distribution of DDoS attacks by day of the week Q4 2019 and Q1 2020.
Amazon Web Services the 800-pound gorilla of everything cloud computing was hit by a gigantic DDoS attack in February 2020. This allows us to normalize the data points and avoid biases towards for example a data center. Accordingly HTTP flooding finished bottom with its lowest score since.
In that case addressing this issue is critical because it will foster the continuity of your. 1 Well execute some targeted attacks and check your DDoS servers by the 500 Gbps attack power 2 We can do multi-vector attacks Layer 3-7 TCP UDP SYN. In 2018 GitHub saw one of the largest DDoS attacks ever recorded.
Most of the Belgium governments IT network has been down today after a massive distributed denial of service DDoS attack knocked offline both internal systems and public-facing websites. Behind todays DDoS attacks youll find botnets and theyre using the same old techniques hackers have always used to bring down your servers. Akamai First you should know that while the total.
Experts say that the DDoS attack came as a response to a political conflict with Russia. The Latest Threats Advisories Attack Reports. That depends on the specific type of DDoS attack being carried out.
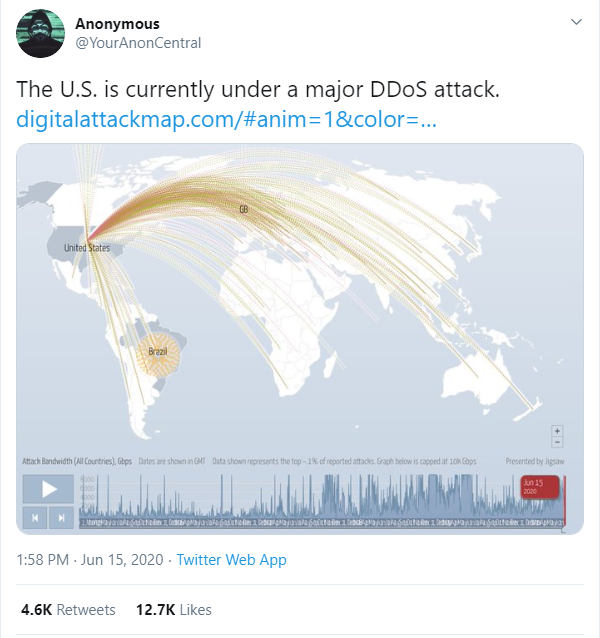
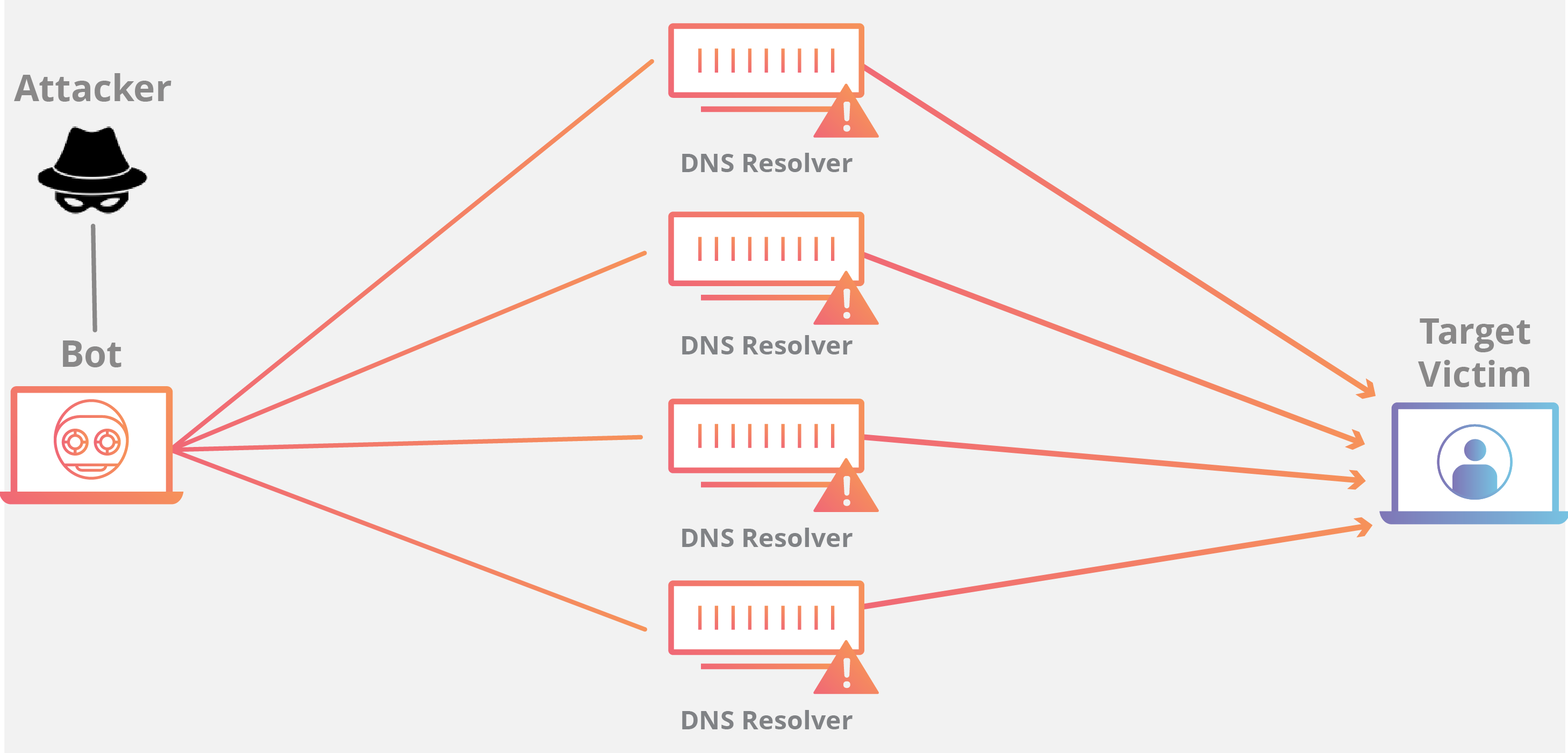
NTP DNS SSDP Amplification. Botnets of malware-infected computers or IoT devices offer one common platform for DDoS attacks. 84 Million 2019 DDoS attacks NetScouts new vulnerability analysis exposes a sad yet undeniable fact of our internet security.
This was the most extreme recent DDoS attack ever and it targeted an unidentified AWS customer using a technique called Connectionless Lightweight Directory Access Protocol CLDAP Reflection. Luckily the company had a mitigation strategy in place and quickly switched to routing traffic through its DDoS protection service foiling the attack. The past quarter has seen some noticeable changes in the distribution of DDoS attacks by type.
A multi-vector DDoS attack uses multiple attack pathways in order to overwhelm a target in different ways potentially distracting mitigation efforts on any one trajectory. While moving your operations online has its added advantage in todays business environment its also imperative to put measures in place to guard against hackers and online attacks. The year 2019 saw a record 84 million DDoS assaults according to NetScout threat intelligence.
ICMP flooding added 2 pp. Recent DDoS attacks have evolved to become a serious threat to the smooth running of both businesses and governments. The FBI issued a report in 2020 stating that cyber actors were starting to disrupt K-12 educational institutions and third-party services supporting remote learning via DDoS attacks.
Stay ahead of the vulnerabilities with updated DDoS reports mitigation best practices and cybersecurity threat reports from Radwares threat intelligence team. New cybersecurity attacks and DDoS threats are lurking in the shadows every day. A distributed denial-of-service DDoS attack involves flooding a target system with internet traffic so that it is rendered unusable.
This means 670000 attacks a month 23000 attacks a day and every minute 16 attacks. Types of DDoS attacks. What does a DDoS attack do and how does it work.
Details of how. The Top Four Practices and Types of DDoS Attacks Used. Today the Estonian DDoS Attack is studied by countries as one of the first-ever and largest instances of cyber-warfare.
There are many different types of DDoS attacks. Well begin massive DDoS attack Today you have 5 hours after reading your posts. This morning a ton of websites and services including Spotify and Twitter were unreachable because of a distributed denial of service DDoS attack on Dyn a major DNS provider.
Today wed like to share the latest DDoS insights and trends that are based on attacks that our system mitigated during the first quarter of 2021. When we analyze attacks we calculate the DDoS activity rate which is the percent of attack traffic out of the total traffic attack clean. This technique relies on vulnerable third-party CLDAP servers.
According to Wired the attack measured 135 terabits of data per second and GitHub suffered from outages as a result. This attack led to the creation of NATOs Cooperative Cyber Defence Centre of Excellence in Tallinn Estonia. The attack targeted Belnet a government-funded ISP that provides internet connectivity for Belgian government organizations such as its Parliament educational institutes.
Still today many people have no and still dont have idea about how to stay safe online and do not know how to respond in critical scenarios.
