As you look around your organization think about how your employees could be. You can use a risk assessment template to help you keep a simple record of.
 Characteristics Or Attributes Of Risk Assessment Methods Download Table
Characteristics Or Attributes Of Risk Assessment Methods Download Table
Identify specific risk categories.

How to perform a risk assessment. This takes the risk assessment and maps internal controls to the risks to determine if there are gaps between risks and controls. 5 Basic Steps for a Risk Assessment 1. Perform a risk assessment based on risk factors.
Managers and employees need to know where they can look for additional information. What is the first step in performing risk assessment. Documentation for risk assessment and management.
Establish groups that are affected by the risks and hazards you. The benefits of that is it helps to reduce the level of uncertainty of those risks on the project and allows us to focus on the high priority risk. Provide narrative guidance to show understanding and justification.
Define levels of uncertainty. Once you have identified sources of risks the next step is to understand how much. The first part we perform a qualitative risk analysis and there what were doing is thats a process of prioritizing the risk for further analysis or action depending upon the probability and the impact of those risks.
Risk assessment template Word Document Format. ISO 27001 doesnt prescribe a single set way to perform a risk assessment. Decide Who Could be Harmed and In What Way.
A risk assessment analysis allows a project manager to prepare in advance for strategic legal. Take the time to. What further action you need to take to control the risks.
When the action is needed by. An internal control assessment can be performed at the same time. Documentation varies depending on the unique needs of your business but might include the processes and.
What is the final step in the risk assessment process. First you should look at your organisations context. Who might be harmed and how.
When to Perform Risk Assessment. Ie monitoring tracking acceptable risk levels. Three steps to complete a risk assessment.
Performing a comprehensive risk assessment analysis to limit vulnerability reduces a projects level of operational strategic and legal risk. Make a list of potential risks that you could encounter as a result of the decision you are. Take a look around your workplace and see what processes or activities could potentially harm.
Identifying risk and control owners helps to clarify roles and responsibilities in the company and promotes accountability. Instead it will help you consider all the possible risks in the workplace and the ways you can keep people safe from these risks. When to Update Risk Assessment.
A risk assessment is not about creating huge amounts of paperwork. The first step in performing risk assessment is to identify and evaluate the information assets across your organization. Who needs to carry out the action.
Risk assessment allows management to assess the companys risks and controls and devote resources where needed. Risk assessment is a simple way to plan what youre going to do to minimise the chances of anybody getting hurt or causing damage to property or equipment. Initial risk estimation and evaluation.
Any risk assessment starts with a review of the current infrastructure. Evaluating the financial impact and likelihood of each risk can be helpful when prioritizing the companys risks. Both hardware and software require an assessment of strengths and weaknesses.
Take a deeper dive into identified risk categories and rate them. Risk Assessment is managements process of identifying risks and rating the likelihood and impact of a risk event. To create a well rounded risk assessment you will need to go through a series of steps to then write the assessment.
How to create a risk analysis 1. Consulting lists developed by safety groups can also help you to look for specific hazards in. To do this you need to review certain things.
5 steps in the risk assessment process 1. At this stage you need to qualitatively evaluate the risk likelihood and severity of each event. Instead you should tailor your approach to the needs of your organisation.
A key construction method or process changes according to the change of design. Determine who might be harmed and how. Assets with security risks should be.
These include servers client information customer data and trade secrets. Risk Assessment must be carried out and associated hazards identified and control measure put in place for all activities before the beginning of the work at site. One important aspect of risk communication is having documentation for the guidelines and controls.
What youre already doing to control the risks. Once the project manager identifies potential problems he should define actions that mitigate or eliminate these situations. New equipment substances and.
 How To Perform A Risk Assessment For Collaborative Robots
How To Perform A Risk Assessment For Collaborative Robots
 How To Perform A Risk Assessment Rethinking The Process Cso Online
How To Perform A Risk Assessment Rethinking The Process Cso Online
Beyond The Basics Steps To Conduct A Risk Assessment
 How To Conduct A Risk Assessment Hsse World
How To Conduct A Risk Assessment Hsse World
 Proposed Steps To Perform Risk Assessment Bullet Training And Download Scientific Diagram
Proposed Steps To Perform Risk Assessment Bullet Training And Download Scientific Diagram
 How To Use A Risk Assessment Matrix With Template
How To Use A Risk Assessment Matrix With Template
 How To Conduct A Risk Assessment 2018 03 01 Assembly Magazine
How To Conduct A Risk Assessment 2018 03 01 Assembly Magazine
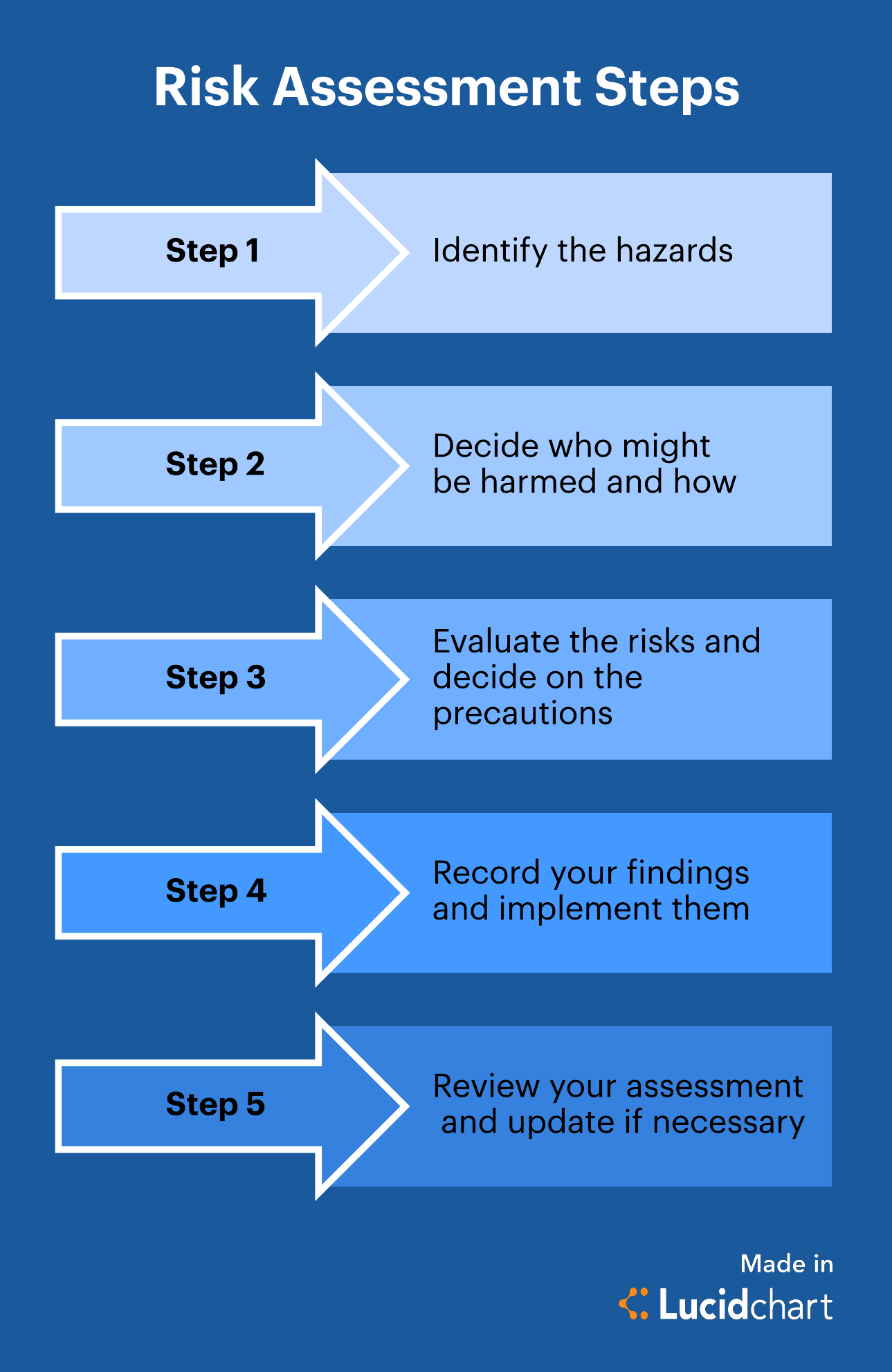 A Complete Guide To The Risk Assessment Process Lucidchart Blog
A Complete Guide To The Risk Assessment Process Lucidchart Blog
 How To Perform Your Own It Risk Assessment By Nordic Backup Medium
How To Perform Your Own It Risk Assessment By Nordic Backup Medium
 A Complete Guide To The Risk Assessment Process Lucidchart Blog
A Complete Guide To The Risk Assessment Process Lucidchart Blog
 How To Perform It Security Risk Assessment
How To Perform It Security Risk Assessment
 Don T Want To Fail Do A Project Risk Assessment
Don T Want To Fail Do A Project Risk Assessment
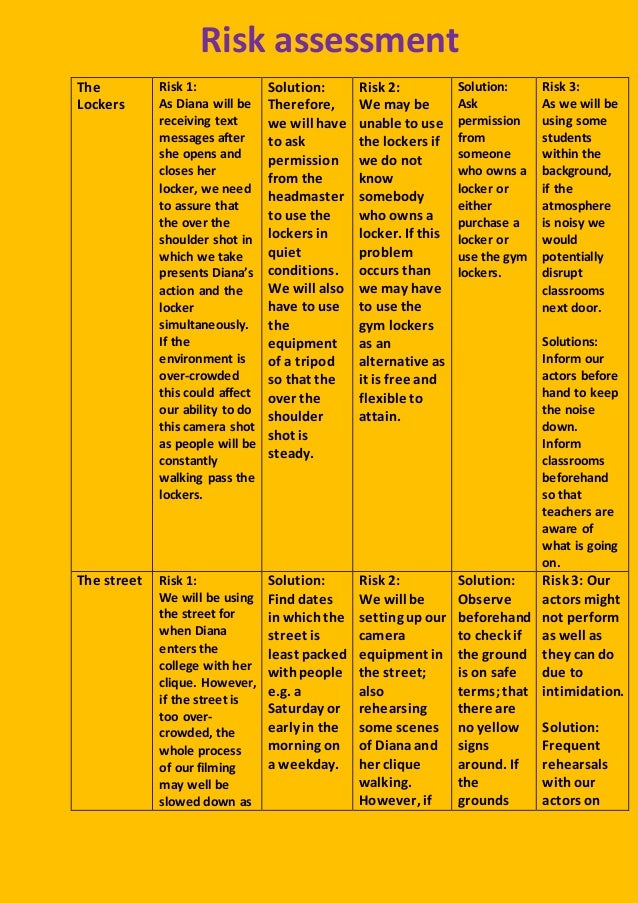 A2 Media Studies Risk Assessment
A2 Media Studies Risk Assessment

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.